Preamble
As of 2022, most everyone in the world with internet also has access to an email account, and the threat of being just one click away from a social engineering attack is very real. For many, seeing emails claiming to be someone else in the attempt to elicit a click is fairly normal; it is a commonplace scenario that we all seem to be presented with often, if not daily.
Etymology
From phishing.org1:
There is also a good reason for the use of “ph” in place of the “f” in the spelling of the term. Some of the earliest hackers were known as phreaks. Phreaking refers to the exploration, experimenting and study of telecommunication systems. Phreaks and hackers have always been closely linked. The “ph” spelling was used to link phishing scams with these underground communities.
Introduction
phish·ing /ˈfiSHiNG/: is defined by the Oxford dictionary as the fraudulent practice of sending emails purporting to be from reputable companies in order to induce individuals to reveal personal information, such as passwords and credit card numbers.
Historically, phishing emails have been poorly constructed and include a far fetched narrative that would cause many recipients to be concerned about clicking on the links inside them, not to mention open the files attached to them, however times have changed. The tactics employed by malicious organizations that operate phishing campaigns have continuously been updated over the years to appear much more legitimate, get past technical and human defenses, and increase their click rates.
While clicking phished links may not result in compromise, it is possible. When used in conjunction with an exploit kit to leverage a vulnerability, a tailored exploit can be delivered to compromise the connecting system.
Where did it start
Since the mid 1990’s, phishing emails have been recognized as a tactic in use1, and a concern for those who use email regularly for business and personal.
From phishing.org:
According to Internet records, the first time that the term “phishing” was used and recorded was on January 2, 1996. The mention occurred in a Usenet newsgroup … where the first rumblings of what would become a major criminal issue would take place.
While the average motivation behind phishing has maintained fairly consistent, to steal sensitive information, the consequences of becoming a victim have drastically been increased.
Prior generations
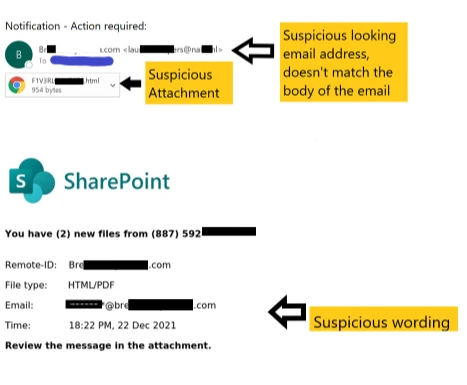
Emails such as this one gamble with the expectation that logos of companies that businesses commonly interact with are sufficient to trick its victim into assuming legitimacy of the content and sender. They normally contain a link to “login” to the legitimate site portrayed to direct its victim to a spoofed version intended to harvest credentials used for the service, or include an attachment with a call to action included in the body of the email to deliver a malware payload.
Links included in an email targeting Microsoft 365 email users for example, may include a fake login page appearing similar to the screen normally presented by the service provider such as below.
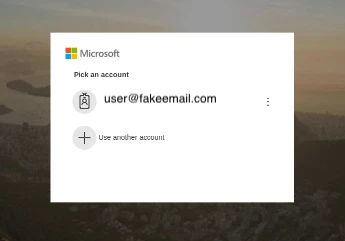
The best defense against something like this is to use trusted bookmarks for sites that you use regularly, and never click links in emails asking you to access them in order to perform some needed action.
Evolution
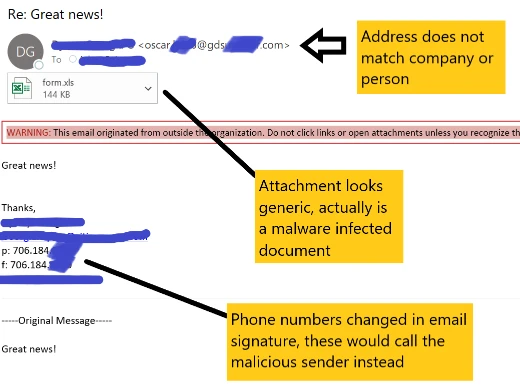
An email like the above has been seen in the wild recently which includes content that appears to have been captured from the mailbox of a compromised recipient that normally receives communications from the impersonated identity. The phishing entity has taken legitimate emails with signatures and mimic the sender directly, along with an added short message at the top to appear as though it is written within a current chain of emails.
The signature in this campaign has often been modified to include a different set of phone numbers that instead call the attacker; most likely to elicit the recipient to question the email and contact them.
It is important to note that this current campaign strictly does not involve the sender specified in the email directly, but indicates a person the infected party are in communication with to extend the amount of time they can operate inside the compromised email accounts.
The next level of this attack could possibly include the complete compromise of an actual account which networks with others and could get past a basic phish test, since the corresponding email address and signatures would be authentic.
Risks explained
Failure to “spot the phish” can result in a victim providing a password or other sensitive information that could be used to gain escalated access to some resource of value that may aid to further compromise the victim.

The fear of business email compromise has never been higher. Criminal organizations target businesses primarily for the purposes of ransomware delivery, extortion, and theft of intellectual property. Businesses are suspected to being targeted more heavily as a result of work from home mandates, with the expectation that it makes employees more susceptible2 to attacks.
Beyond these risks include the fear of penalties imposed by regulatory bodies. As the battle to secure data wages on, rulings such as the one recently passed by the FTC regarding the updated “Safeguards rule”, attempt to close gaps found in some industries where highly sensitive information is handled and processed, in attempt to bring about a more secure environment.

Security awareness
There are many companies who are working to secure the workforce against these types of threats. But there are also many resources to be had that you can use to help yourself with as well.
- https://www.cisa.gov/cisa-cybersecurity-awareness-program
- CISA Cybersecurity Awareness Program
- https://www.cisa.gov/publication/cisa-cybersecurity-awareness-program-toolkit
- CISA Cybersecurity Awareness Program Toolkit
Know of other resources that should be on this list? Contact me.
Resources
These companies provide services to combat phishing attacks.
- https://knowbe4.com
- Security awareness training and phish testing services
- https://www.rapid7.com/
- Security services and training
- https://www.sophos.com/en-us/products/phish-threat
- Phishing training
- https://www.slashnext.com/
- Email phishing protection services
Know of other resources that should be on this list? Contact me.
Related information
According to a report by the FBI in 20203:
Between January 2014 and October 2019, the Internet Crime Complaint Center (IC3) received complaints totaling more than $2.1 billion in actual losses from BEC scams using two popular cloud-based email services. While most cloud-based email services have security features that can help prevent BEC, many of these features must be manually configured and enabled.
Related materials
- Rapid7 makes available this poster detailing some of the important artifacts to look for in identifying phishing emails.
image source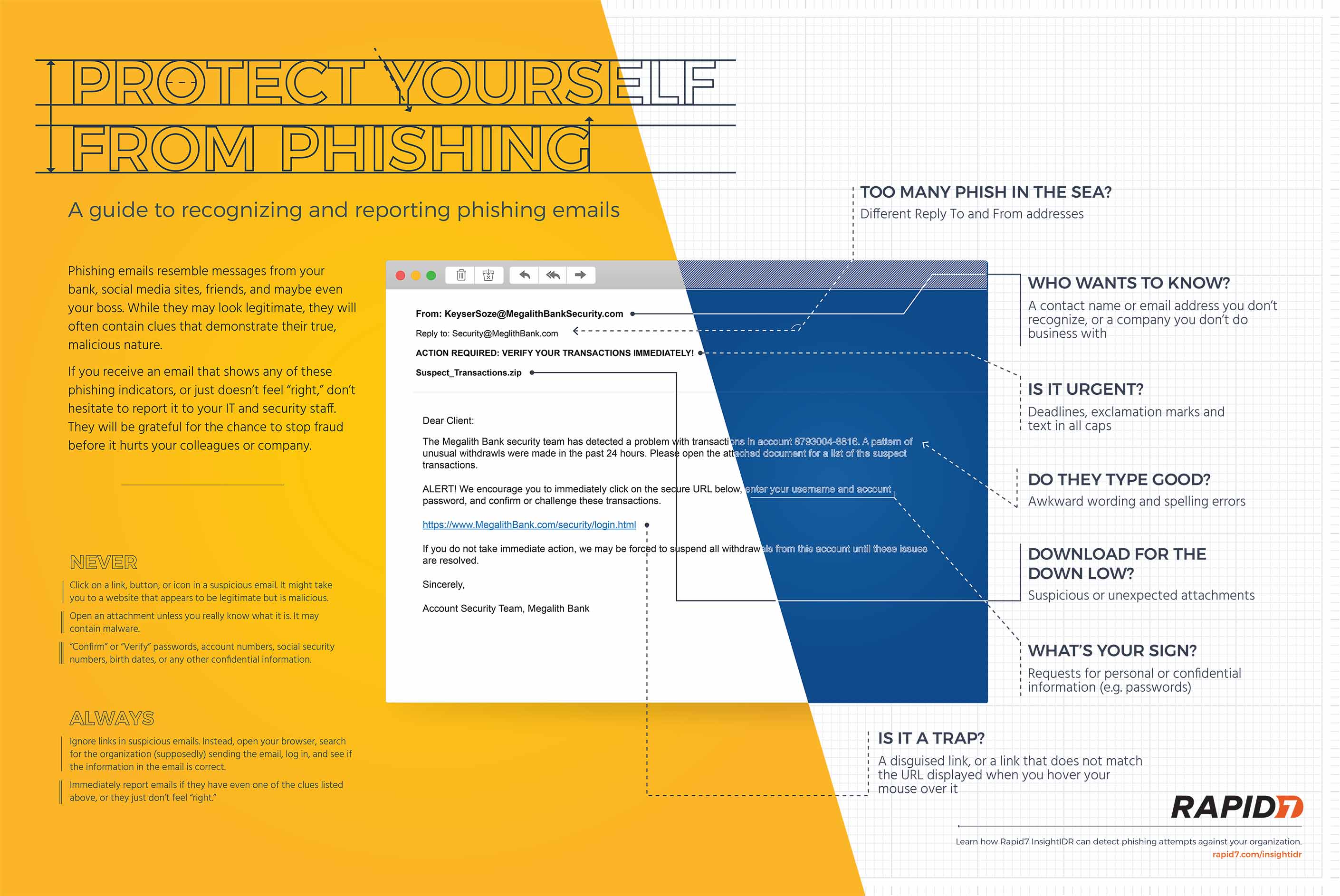
Update #1
It appears the crux of this new phishing campaign is the attackers are attempting to hide the original victim of the phishing content. They are taking content from emails that were received by the original victim and using it to phish people they are in contact with.
Summary
We are continuously being bombarded by social engineering attacks in the form of unsolicited emails. Phishing emails have continually been upgraded in order to become more effective at increasing the success rates of compromise. A business email compromise most likely leads to a breach of data confidentiality.
It’s more important than ever to train employees and yourself on the signs of phishing emails, and to be skeptical of the content they are receiving.
Have any questions, comments, or suggestions? Please leave a comment below or reach out to me here.
Sources
comments powered by Disqus