Introduction
As multi-factor authentication (MFA) has become a standard component used in boosting the level of confidence in the authentication process, techniques employed by threat actors are continuing to evolve and bypass these additional layers.
MFA is an added layer of security, and it’s often seen as a way to help mitigate some of the issues associated with passwords. Poor password strength, password reuse, or the manner in which the password is transmitted and/or stored in the application being accessed are just a few of the associated concerns.
The MFA we make use of today is based upon technology made commercially available by the company RSA through use of key fobs that used codes that changed based on an algorithm used in conjunction with a secret key.
Standards
The National Institute for Standards and Technology, commonly known as NIST, helps to produce the standards used by US Federal government systems and generates a wealth of information regarding the standards for security and privacy as it relates to information systems and organizations.
According to NIST SP 800-63-3 1:
The strength of authentication systems is largely determined by the number of factors incorporated by the system — the more factors employed, the more robust the authentication system
The original multi-factor authentication system paradigm incorporates up to three categories of factors as means to validate access:
- Something you know (e.g., a password).
- Something you have (e.g., an ID badge or a cryptographic key).
- Something you are (e.g., a fingerprint or other biometric data).
Most multi-factor systems will incorporate a password and a code, similar to RSA’s design, however, there are newer methods such as push notifications paired with an authenticator app by Microsoft or Okta that will send a notification to the user’s device and require an interaction to allow the login to occur. These apps also can be protected by biometrics or a pass code, further increasing the security of the accounts protected. Microsoft also takes security a step further with passwordless access - this will be explored in a future article.
Note
While lengthy, the NIST SP 800-53 includes a fairly comprehensive list of controls that are designed for broad use in public and private sector organizations. In the document, it details controls regarding both privileged and non-privileged accounts, noting privileged accounts should have MFA enabled, but today, it is common to see MFA as a requirement for all accounts to obtain cybersecurity insurance.
Why MFA?
There are more downsides to not enabling MFA than to enable it, for example:
…our telemetry tells us that more than 99.9% of organization account compromise could be stopped by simply using MFA, and that disabling legacy authentication correlates to a 67% reduction in compromise risk (and completely stops password spray attacks, 100% of which come in via legacy authentication)…
While MFA may seem as only a benefit to the account holder in preventing access from unauthorized use, it also provides means of maintaining and/or recovering access to the account should someone be able to access it without it enabled.
According to KrebsOnSecurity.com 3:
… people who don’t take advantage of these (MFA) added safeguards may find it far more difficult to regain access when their account gets hacked, because increasingly thieves will enable multi-factor options and tie the account to a device they control.
In Mr. Kreb’s article, he details a story about a child’s Xbox account that was compromised due to password reuse and because they had not yet enabled MFA on their account, the account takeover by the attacker was made much more difficult to unwind.
Most services trust the “second factor” a great deal even to the point where he mentions in his article that Microsoft’s policy “… was not to turn over accounts to someone who couldn’t provide the second factor …”
While the example in this instance was an Xbox account, it could just as well be any account that wasn’t secured with MFA.
Advances in MFA
MFA has matured to include quite a number of additional facets that allow a user to be more secure. While these are not offered universally, they can be useful to consider when taking the time to setup for an enterprise deployment. Examples of additional facets in MFA include geofencing the login to a specific area of the world or limiting time of day to what’s reasonable.
MFA Studies
Google has long been studying the security of MFA in conjunction with the security of the systems its employees make use of.
In a study they published 4 in May ‘19:
We found that an SMS code sent to a recovery phone number helped block 100% of automated bots, 96% of bulk phishing attacks, and 76% of targeted attacks.
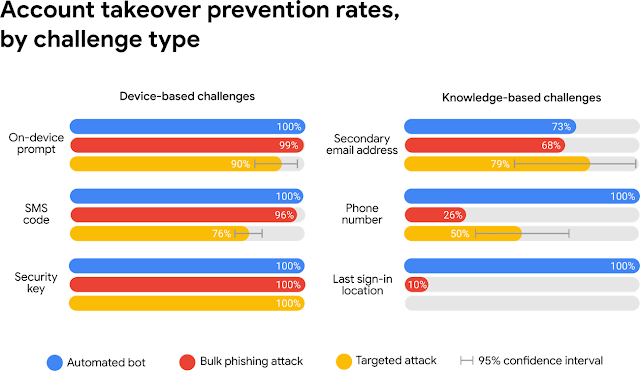
SMS or text-based MFA, is viewed as a low security factor, since texting occurs over a public system with relatively low security. The SIM (Subscriber Identity Module) historically was located on a card physically stored in a phone, however now they are often digital and moved around between devices. A phone with your SIM data will be capable of receiving text messages, including MFA codes.
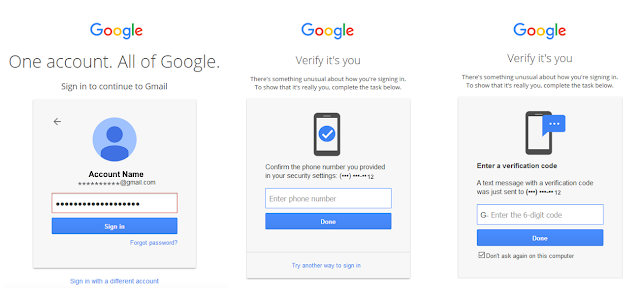
Even though this type of factor is considered insecure, according to Google in 2019, it was sufficient to block a significant amount of attacks against an account. In absence of any other methods, this still provides more security, however better options do exist today which should be used instead when designing secure systems.
Note: NIST (in SP 800-63) does not recognize SMS based MFA codes as a valid multi-factor authentication method due to how easy it can be to obtain these codes by a threat actor.
Bypassing MFA
Phishing emails have been increasingly challenged by the advent of MFA. Threat actors have not been without a response, as some phishing kits have been seen to include a reverse proxy which acts as a man in the middle attack to gain access to the session created during authentication. This token would then provide unauthorized access to the attacker.

This process happens in most cases transparently, and without any awareness by the individual expecting legitimate access, however, most typically this process begins with a phishing email.
This is a topic that will be explored further in the near future.
Summary
Account security will continue to be challenged by threat actors as technology evolves. It is worth noting that nothing can be completely secure, and as you move closer to ideal security, you’re generally moving away from usability. While MFA is not a perfect solution for all use cases, it does provide worthy mitigating techniques that allow for a reduction in attack surface and an increase in confidence that a system will not incur unauthorized access.
Bookmarks
- NIST SP 800-37
- NIST SP 800-53
- NIST SP 800-63
Sources
-
https://www.nist.gov/blogs/cybersecurity-insights/back-basics-whats-multi-factor-authentication-and-why-should-i-care ↩︎
-
https://docs.microsoft.com/en-us/azure/active-directory/fundamentals/concept-fundamentals-security-defaults ↩︎
-
https://krebsonsecurity.com/2020/06/turn-on-mfa-before-crooks-do-it-for-you/ ↩︎
-
https://security.googleblog.com/2019/05/new-research-how-effective-is-basic.html ↩︎
comments powered by Disqus