Introduction
According to cisa.gov 1, ransomware is defined as:
… an ever-evolving form of malware designed to encrypt files on a device, rendering any files and the systems that rely on them unusable. Malicious actors then demand ransom in exchange for decryption.
What specifically defines this malware variant is how it holds its victims hostage, demanding payment to decrypt the impacted devices. However, due to many companies seeing the rising need to increase security against cyber threats, ransomware groups have progressed their tactics in order to adapt by further extorting its victims via threatening the release of sensitive documents if they refuse2. A partial list of variants to date is quite staggering to see3, and expected to rise in volume for the foreseeable future.
Trust
Some groups behind these attacks may honor their claims to decrypt or provide decryption keys to reverse the effects of the infection, but it has been suspected (and proven) that in some cases the original infection may be removed, but later replaced with another group’s malware, perpetuating the cycle.
Ransomware has evolved into a sustainable business model for some would be criminals which depends on trust or fear of public embarrassment of the infected entity to pay. With such polarizing discussion surrounding whether or not to pay these ransoms, there isn’t a one size fits all answer, but knowing the threats and developing a playbook for this scenario is certainly important.
Attack Vectors
The two most common attack vector for ransomware tends to be via the exploitation of a software vulnerability4 and email attachments or links5.
Exploitation of software
In the post by Checkpoint 4, they refer to a vector of attack via RDP compromise:
With RDP, an attacker who has stolen or guessed an employee’s login credentials can use them to authenticate to and remotely access a computer within the enterprise network. With this access, the attacker can directly download the malware and execute it on the machine under their control.
While this attack vector isn’t normally accessible without first gaining access into a network, there has been a significant number of hosts found exposing RDP publicly using a simple search through a service named Shodan 6.
Exploit kits
While exploits are usually the first phase of an attack, exploit kits can be deployed to apply ransomware to a successfully compromised device. In essence, exploit kits are devised to be fully automated, and generally make use of compromised sites used to scan for vulnerable browsers and add-ons. Should the exploit kit find a vulnerable software it can exploit, it deploys the correct module designed to compromise it. You can think of an exploit kit as a multi-tool device that can be adapted to the needs of the circumstances.
This graphic visualizes how an exploit kit may be used to compromise your device after visiting a site either being operated by an attacker or a site which has been compromised to host malicious code.
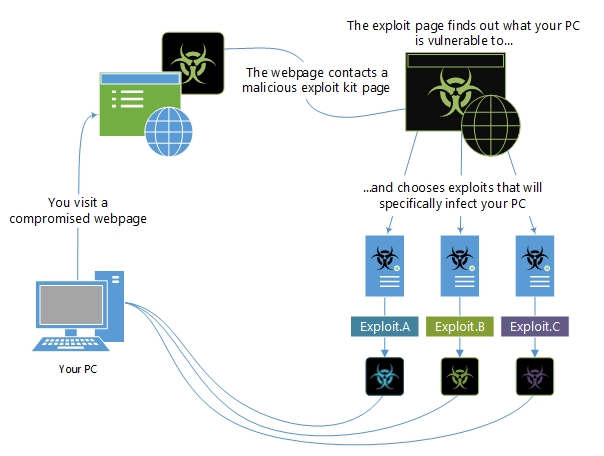
One of the top protection strategies against exploit kits is making sure you keep your software up-to-date as much as possible. The majority of exploit kits typically leverage zero-day threats which are quickly weaponized by groups that spread ransomware to take advantage of the mean time to patch (MTTP), which for many organizations can be as long as 60 to 150 days7, however, organizations prioritizing security would ensure to apply patches that pose a serious threat within a significantly lower period. Unfortunately, a side effect to the production of patches rapidly is that the patch itself can produce additional vulnerabilities or instability.
A typical suggested8 manner for patching systems tends to have multiple phases and requires good standards in place to ensure that testing reflects real world scenarios.
Email attachments
Emails with malicious attachments are typically coupled with the body of the email to create a scenario crafted to socially engineer the recipient into opening an attachment that may appear similar to the below image9.
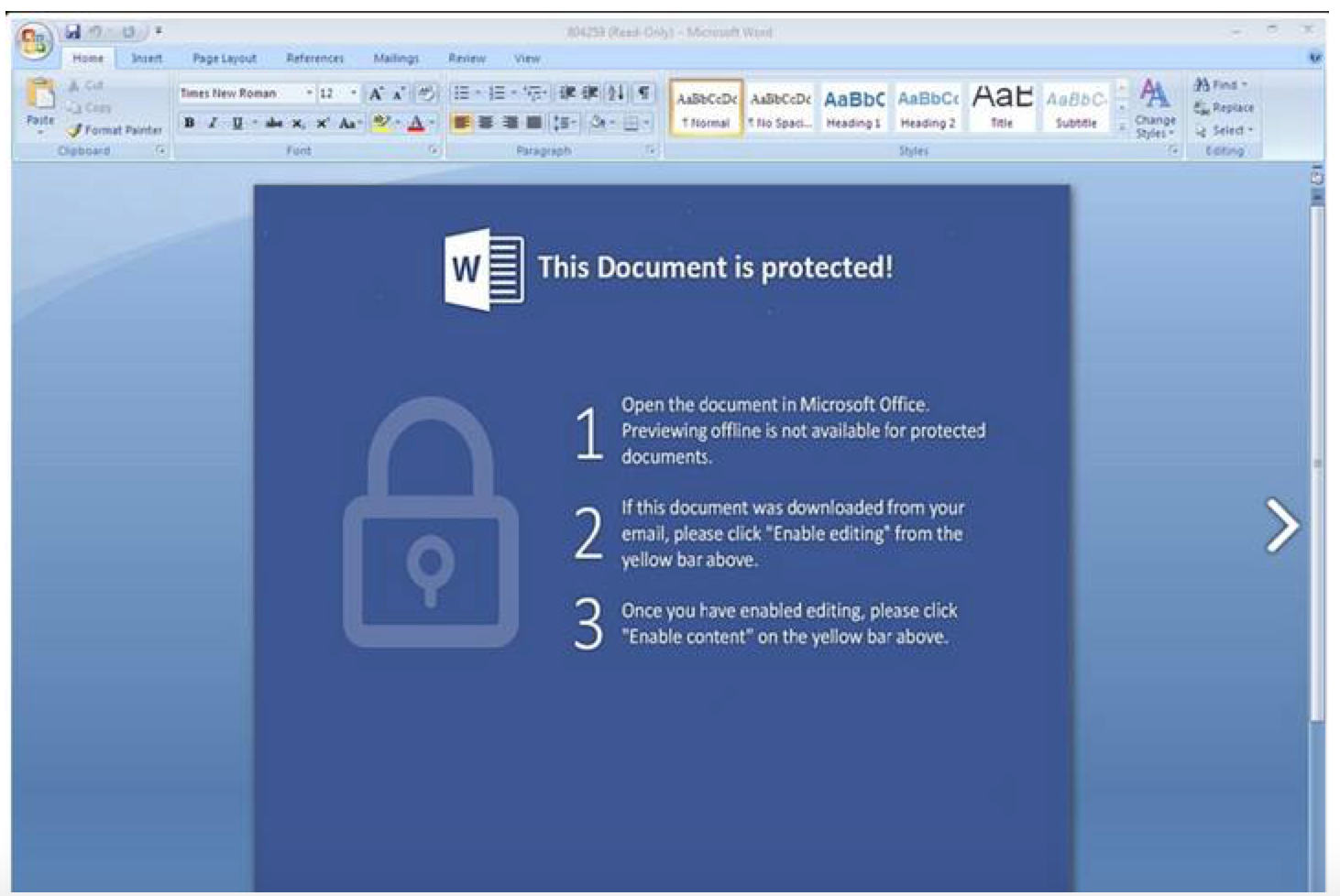
The email may have such pretexts as it includes an encrypted document that must be opened with a password provided in the email. Recipients may be inclined to ignore warnings prompted by the application, which indicate only to disable these protections if they understand the risks.
Generally these types of documents utilize a word document macro which is typically an obfuscated powershell command to download and execute a payload on the executing host device.
These powershell scripts are typically in communication with Command and Control servers that help deliver the ransomware payload to persist on the endpoint device.
Side notes
Previous Senior Applied Security Researcher at Mandiant / FireEye, and current Security Researcher at Microsoft, Daniel Bohannon discusses an interesting topic of detecting obfuscated powershell here .
Ratnesh Pandey from Security Boulevard dives into an example obfuscated malicious powershell script here .
Email links
Just link attachments, emails that are tailored to phish a recipient of an email is most commonly devised to deliver, in some manner, some form of ransomware.
Specific emails targeting online services that are used by people in their everyday jobs are typically referred to as campaigns. These emails are currently the most prevalent type of phishing that occurs as it may look familiar to the individuals receiving them, causing them to lower their suspicion of malintent.
A good strategy against this type of attack includes:
- User awareness training
- Companies such as KnowBe4 provide user training for this, transforming you into a better “human sensor”
- If using an email provider offers “Safe Link” technologies, make sure to enable it if required
As business email compromise continues to be an attack vector used by malicious threat actors, the need to continually expose yourself and others to awareness training is important. As the last line of defense, it’s paramount to be vigilant against threats that pass through filters of automated systems and improve our ability to identify the signs of deception.
Before it happens
I purport that everyone will eventually be exposed to a ransomware attack given an infinite amount of time and a lack of appropriate security measures that guarantee prevention. So the best prepared will have the opportunity for the best outcome.
So before you’ve been hit, it’s best to have a plan in place to know how you’re going to respond. The Cybersecurity & Infrastructure Security Agency posts a guide to be help be prepared and respond to an attack.
Some key takeaways from the CISA Ransomware Guide :
Apply the principle of least privilege to all systems and services so that users only have the access they need to perform their jobs. Threat actors often seek out privileged accounts to leverage to help saturate networks with ransomware.
The benefits of this concept should go without saying. Do not operate at a permission level higher than necessary to carry out the tasks you need. Elevating to those permissions as necessary will reduce overall risk.
Employ logical or physical means of network segmentation to separate various business unit or departmental IT resources within your organization as well as to maintain separation between IT and operational technology. This will help contain the impact of any intrusion affecting your organization and prevent or limit lateral movement on the part of malicious actors.
If you reduce the scope for which attackers have access to, you in theory reduce the amount of risk you expose to an attacker.
Employ MFA for all services to the extent possible, particularly for web-based email, virtual private networks, and accounts that access critical systems.
This has become more important than ever as more and more people are working remotely or working from home. While all types of MFA aren’t equal, especially if you’re using SMS as the authenticator, it will greatly increase the effort necessary to compromise accounts. It is recommended that an authenticator app or hardware token where feasible.
Most importantly, back up regularly and keep a recent backup copy off-site. The gold standard for backup methodology is the 3-2-1 method. There should be three copies of the data, with two different types of media, and one of the copies in an off-site location in case of disaster recovery.
Several providers offer specific backup strategies targeted around the concept of ransomware data protection and recovery. One such provider is Druva .
After it happens
Should you be involved in a ransomware attack, the following essentials should be performed10:
- Determine the impact
- Isolate affected devices
- Triage recovery of systems based on business impact
- Work with an experienced incident response team to analyze what occurred
- Engage with teams and stakeholders to establish communication and deliver a consistent message
In an article by Kurt Baker of Crowdstrike 11:
… the difference between a business-sinking infection and a minor network interruption can come down to reaction time. Businesses must swiftly cut or restrict network access to stop the spread from infected devices.
The steps he outlines are important to follow, not excluding the reporting of the incident. In 2022, if you suffer a ransomware attack, it’s most definitely a breech. Penalties for not disclosing breeches can be significant.
As ransomware typically involves the threat of data leaks, any attack should be reported to the relevant authorities as soon as possible.
…if you suffer a data breach in California for example, you must report it to the CCPA, and any individual violation results in $7,500 fines per violation.
Pull out your playbook guide designed from using the CISA Ransomware Response Guide , stay calm and trust the process.
Ransomware News
Microsoft says dozens of computer systems at an unspecified number of Ukrainian government agencies have been infected with destructive malware disguised as ransomware. https://t.co/LZy8CIZRvj
— The Associated Press (@AP) January 16, 2022
A ransomware incident last week against Bernalillo County, N.M., had far-ranging consequences at the county's jail, which has mostly confined its inmates to their cells since the cyberattack disabled the facility's surveillance cameras https://t.co/vFsvlWkAcv pic.twitter.com/QrTWRc0ltj
— StateScoop (@State_Scoop) January 15, 2022
Summary
As companies become more aware of the threats posed to them, the threats will continue to evolve and find gaps in security where they exist. Most common threats exploit vulnerable software, misconfiguration, or lack of awareness and/or training in the people who use these systems. Focusing on these areas will help reduce overall risk exposure to ransomware and other threats.
Sources
-
https://www.darktrace.com/en/blog/double-extortion-ransomware/ ↩︎
-
https://www.crowdstrike.com/cybersecurity-101/ransomware/types-of-ransomware/#examples ↩︎
-
https://www.checkpoint.com/cyber-hub/threat-prevention/ransomware/ ↩︎
-
https://www.paloaltonetworks.com/cyberpedia/ransomware-common-attack-methods ↩︎
-
https://resources.infosecinstitute.com/topic/how-to-discover-open-rdp-ports-with-shodan/ ↩︎
-
https://securityintelligence.com/posts/how-do-you-measure-the-success-of-your-patch-management-efforts/ ↩︎
-
https://security.gatech.edu/patch-management-best-practices ↩︎
-
https://nakedsecurity.sophos.com/2017/04/24/ransomware-hidden-inside-a-word-document-thats-hidden-inside-a-pdf/ ↩︎
-
https://www.cisa.gov/stopransomware/ive-been-hit-ransomware ↩︎
-
https://www.crowdstrike.com/cybersecurity-101/ransomware/#How-To-Respond ↩︎
comments powered by Disqus